The arrival of WEB 2.0 brought dynamic content through the use of technologies such as Java, Flash and PHP.
Consequently it also widen the attack surface. Websites became prettier, more interactive, easier to update and also easier to attack!
The need for further functionality was, as it is often the case, at the cost of security.
The four diagrams below illustrates the differences between a WEB 1.0 and a WEB 2.0 architecture as well as highlighting the increased attack surface.
In a typical WEB 1.0 architecture, besides the physical, human and network security considerations, protecting the data is dependant of the Operating System and the application security layers. Typically, the application security layer is restricted to the Web Server (i.e.: Apache) if no other services/applications are exposed to the Internet.
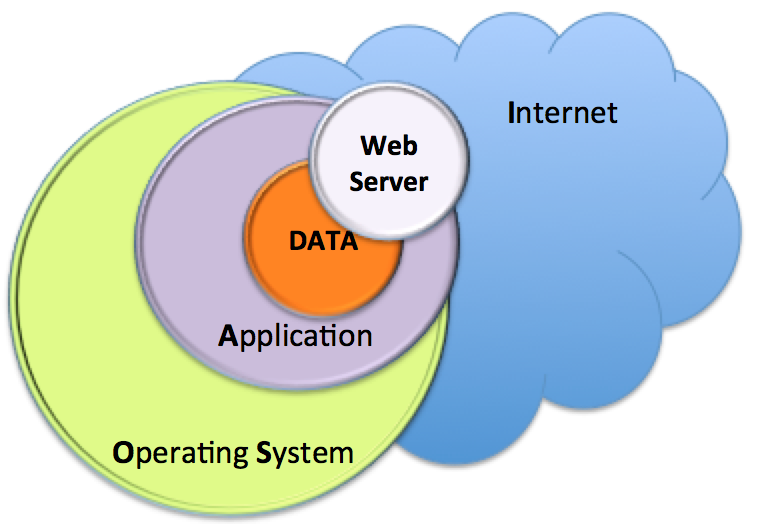
Diagram 1 - WEB 1.0 Typical Ar...
>>[READ MORE]

 RSS Feeds
RSS Feeds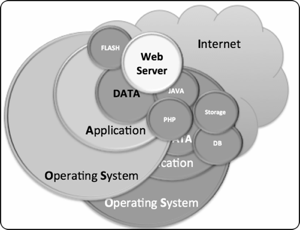 How to reduce WEB 2.0 attack surface by going back to WEB 1.0, the dynamic way!
How to reduce WEB 2.0 attack surface by going back to WEB 1.0, the dynamic way!
 SELKS 2.0 vs. Security Onion
SELKS 2.0 vs. Security Onion