As our world reliance on electronic connection and communication is accelerating, cyber attacks are on the rise along with
counter measure solutions in the form of endless new cyber security companies, consultants, expertise, software and hardware
aimed at protecting individuals, assets, corporations and even nation states.
However, even with all the tools and increasing cyber budget at our disposal, there is always one constant weak link:
The Human element in the so called Cyber Kill Chain.
It is this human element that can defeat the most sophisticated defence systems and it is why the use of Phishing and
Spear Phishing attacks are so prominent and successful.
Those attacks exploit human emotion, ignorance and credibility to bypass defences in tricking users to follow poisonous steps:
Clicking on links, opening documents, accepting/ignoring security warnings and good practises, installing software, etc....
>>[READ MORE]
 How to build a Red Team and Why?
How to build a Red Team and Why?
#115 - Posted on
11 November 2015 - Author: SM - Category: Conferences, Security, Hacking, Guides
I recently gave a talk at the Rant Forum in London on the topic of
"RedTeam, why this is more than a buzz word?".
It was an interesting experience and whilst different from traditional security events, as the crowd can and will interrupt you at any time, it was very enjoyable.
Many attendees asked if I could produce some "slides" after the talk. As no slides were used, below is a collection of notes from wich the talk was based on.
In this post we will explain what RedTeam is, how does it fit with other similar security services and what advantages does it bring to an organisation.
We will also look into what works? what doesn’t? And where is this “new” type of service going?
1. DEFINITION
A Red Team is part of a trio of services which increases in sophistication: Vulnerability Assessment, Penetration Testing and then Red Teaming.
We will d...
>>[READ MORE]
 One more update to the Security Onion Guide
One more update to the Security Onion Guide
#103 - Posted on
11 May 2015 - Author: SM - Category: Guides, IDS, Misc, Security
We have updated once more our Security Onion Installation Guide with a few tweaks regarding setting up BRO emails and SSH.
There is also a new PDF version, using an updated template, available from the download section .
...
>>[READ MORE]

 RSS Feeds
RSS Feeds How to secure your mobile phone and check for spyware?
How to secure your mobile phone and check for spyware?
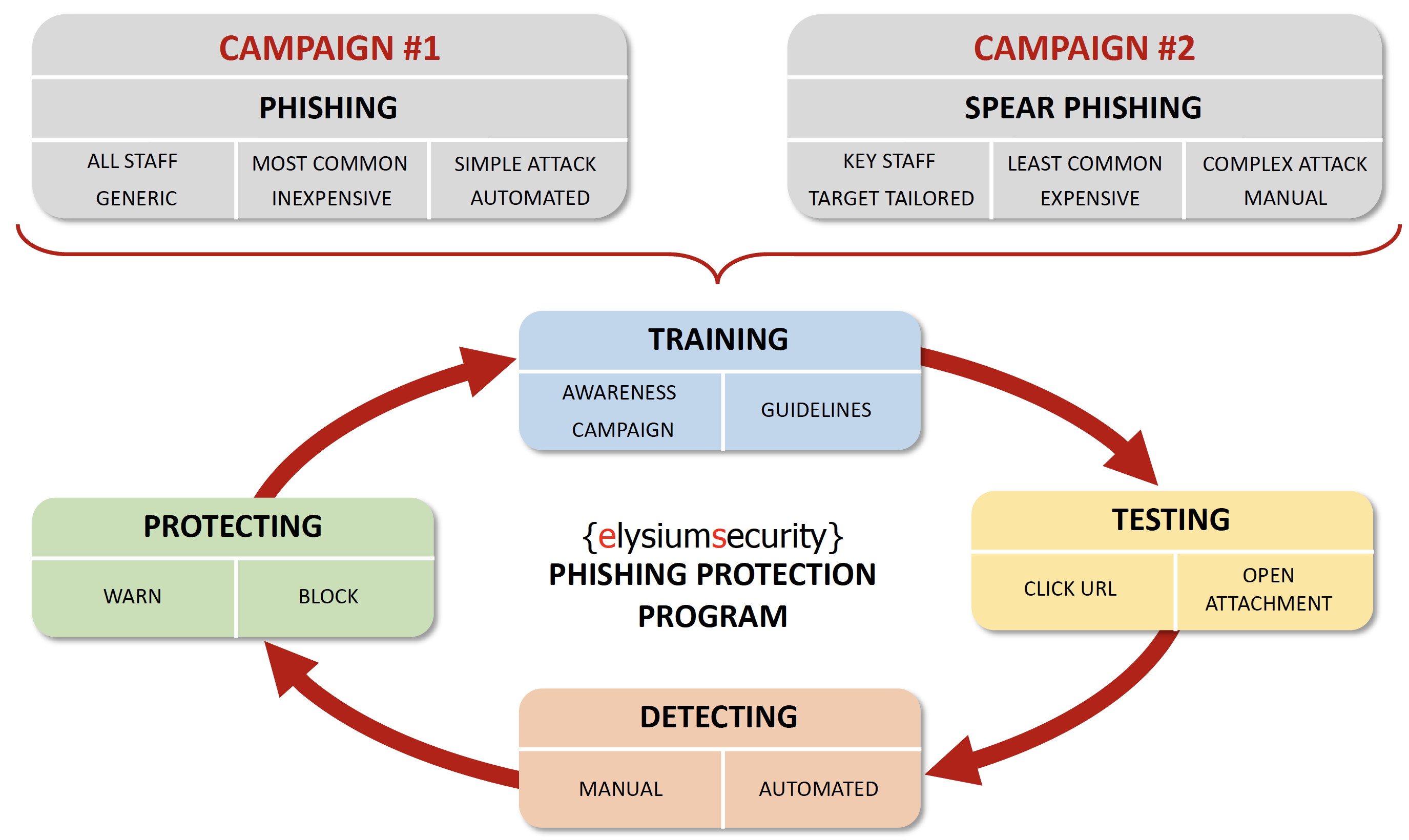
 Cyber Security Planning - A simple 6 Steps Approach
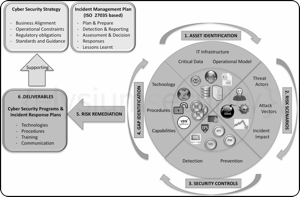
Cyber Security Planning - A simple 6 Steps Approach
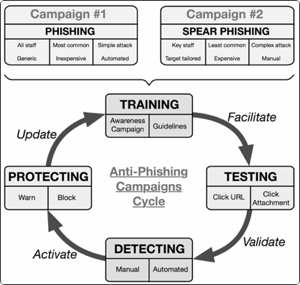 How to build an efficient Anti-Phishing Framework?
How to build an efficient Anti-Phishing Framework?