As our world reliance on electronic connection and communication is accelerating, cyber attacks are on the rise along with
counter measure solutions in the form of endless new cyber security companies, consultants, expertise, software and hardware
aimed at protecting individuals, assets, corporations and even nation states.
However, even with all the tools and increasing cyber budget at our disposal, there is always one constant weak link:
The Human element in the so called Cyber Kill Chain.
It is this human element that can defeat the most sophisticated defence systems and it is why the use of Phishing and
Spear Phishing attacks are so prominent and successful.
Those attacks exploit human emotion, ignorance and credibility to bypass defences in tricking users to follow poisonous steps:
Clicking on links, opening documents, accepting/ignoring security warnings and good practises, installing software, etc....
>>[READ MORE]
{elysiumsecurity} 
Cyber Protection & Response
All News (146 Posts)
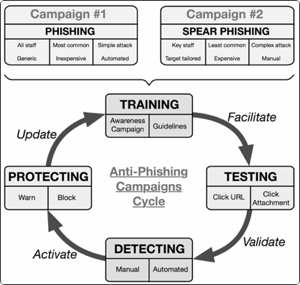 How to build an efficient Anti-Phishing Framework?
How to build an efficient Anti-Phishing Framework?
 How to build a Red Team and Why?
How to build a Red Team and Why?
I recently gave a talk at the Rant Forum in London on the topic of
"RedTeam, why this is more than a buzz word?".
It was an interesting experience and whilst different from traditional security events, as the crowd can and will interrupt you at any time, it was very enjoyable.
Many attendees asked if I could produce some "slides" after the talk. As no slides were used, below is a collection of notes from wich the talk was based on.
In this post we will explain what RedTeam is, how does it fit with other similar security services and what advantages does it bring to an organisation.
We will also look into what works? what doesn’t? And where is this “new” type of service going?
1. DEFINITION
A Red Team is part of a trio of services which increases in sophistication: Vulnerability Assessment, Penetration Testing and then Red Teaming.
We will d...
>>[READ MORE]
 RANT FORUM - Red Team Recipes Presentation
RANT FORUM - Red Team Recipes Presentation
I will be giving a talk tomorrow evening, the 28th of November at around 6pm, in London at the Risk and Network Threat (RANT) Forum .
The topic is:
Why RedTeam is more than just a buzz word? What works? What doesn't? And where is this "new" type of service might be going? All those questions answered by someone who is actually delivering Red Team activities.
Registration is free, you get free drinks and food... plus you get to hear me talk, so what is not to like?! :)
You can register HERE
The RANT Forum is quite different from your typical free security briefing, for a start it is not a sales forum. However, the company behind it is a recruitment agency, so they are still interested in taping the UK Security professional community!
...
>>[READ MORE]
 IDS used as a Network Forensic Tool
IDS used as a Network Forensic Tool
Note: This is the second post of a two parts series on how to use IDS in a different way.
Intrusion Detection Systems are traditionally seen as Defensive tools. They can however be used for different purposes than initially designed for as highlighted in the previous post , where we discussed how IDS could be used as an offensive tool.
The popularity of pre-configured/packaged IDS environments such as SELKS or Security Onion provide various software packages and Graphical User Interfaces to navigate through large volume of data by parsing/categorising/filtering it automatically.
More importantly, such systems are starting to provide mo...
>>[READ MORE]
 IDS used as an Offensive Security Tool
IDS used as an Offensive Security Tool
Note: This is the first post of a two parts series on how to use IDS in a different way.
Intrusion Detection Systems such as Snort and Suricata
are traditionally seen as Defensive tools, and in essence they are. They can alert on security issues occurring on your network such as Botnet Activities, network based attacks, hosts/servers activities and vulnerabilities.
That last point is important.
It is important because that same information used for defence activities, could be used by an attacker as part of an attack reconnaissance. For example, being able to identify a list of hosts that use outdated SSH/SSL servers, a vulnerable Flash Client or other vulnerable software/services; HTTP logs highlighting users web activities, clear text passwords, etc.
When looking at an IDS that way, it becomes a passi...
>>[READ MORE]
 Securing your Cloud Storage with a Boxcryptor alternative called EncFS
Securing your Cloud Storage with a Boxcryptor alternative called EncFS
Cloud storage providers such as Dropbox, Box, One Drive, etc. are increasingly being used for both personal and business reasons. On the Business side, often without the individual's company fully aware of what data is actually leaving their premises.
One of the issue with storing data in the cloud is Security. Looking at Dropbox in recent years, there has been a number of embarrassing blunders which resulted in their customers' data becoming available to anyone who knew where to look. We did blog about it several times: here, here and here. Many other security blogs also related those stories, such as this nice summary from Sophos.
To limit the risks relat...
>>[READ MORE]
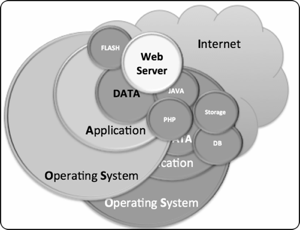 How to reduce WEB 2.0 attack surface by going back to WEB 1.0, the dynamic way!
How to reduce WEB 2.0 attack surface by going back to WEB 1.0, the dynamic way!
The arrival of WEB 2.0 brought dynamic content through the use of technologies such as Java, Flash and PHP.
Consequently it also widen the attack surface. Websites became prettier, more interactive, easier to update and also easier to attack!
The need for further functionality was, as it is often the case, at the cost of security.
The four diagrams below illustrates the differences between a WEB 1.0 and a WEB 2.0 architecture as well as highlighting the increased attack surface.
In a typical WEB 1.0 architecture, besides the physical, human and network security considerations, protecting the data is dependant of the Operating System and the application security layers. Typically, the application security layer is restricted to the Web Server (i.e.: Apache) if no other services/applications are exposed to the Internet.
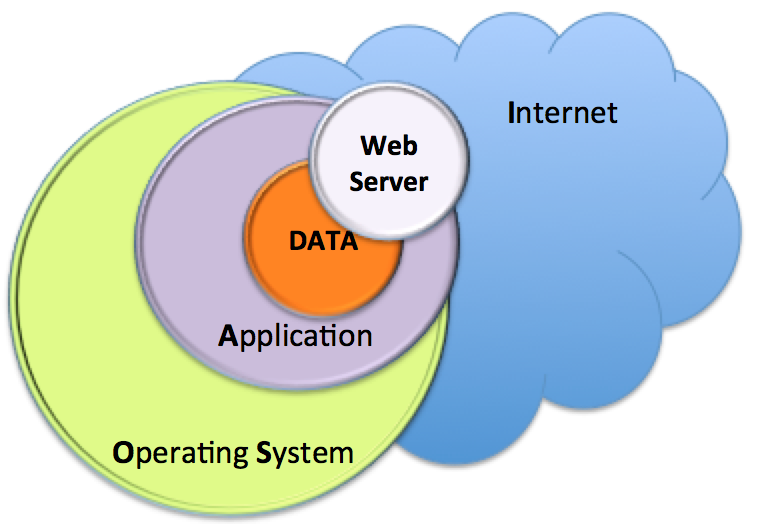
Diagram 1 - WEB 1.0 Typical Ar...
>>[READ MORE]
 Website update
Website update
We have completed our latest website refresh and you may have to reload the various pages to see the new version.
This update brings more information about the different services we offer and how we position ourselves. It also provides better infographics which should make navigating through the site easier to the eye.
We are planning another minor update to our blog section in the coming weeks which will improve your RSS experience.
>>[READ MORE]
 SELKS 2.0 vs. Security Onion
SELKS 2.0 vs. Security Onion
I have recently been testing SELKS v2.0 which is an open source Network Security Monitor (NSM) based on an
ELK framework: Elasticsearch (search and analytics engine) Logstash (log normalisation) Kibana (visualisation).
The NSM core engine is provided by the first "S" which stands for Suricata (Network IDS) and the last "S" which stands for Scirius (Management GUI for Suricata).
SELKS is provided as a live Linux distribution based on Debian 8 (Jessie) which is also installable.
SELKS V2.0 is a great improvement from SELKS V1.0, so much so that I now consider it a serious contender to Security Onion (SO) at...
>>[READ MORE]
 BlackHat Mobile Security Summit - London 2015
BlackHat Mobile Security Summit - London 2015
In June 2015 I attended the Blackhat Mobile Security Summit in London, a 2 days event filled with talks from various researchers and security professionals, there was a 3rd day in the form of a workshop for anyone attending the Interop London hosting event
Blackhat is historically a USA based event with its main conference taking place in Las Vegas every year, lately they started to host similar (but smaller) conferences around the world such as in Singapore and Amsterdam (which I blogged about last year here).
This London edition was definitely on the "smaller" side and this actually had a few advantages:
The quali...
>>[READ MORE]
 RSS Feeds
RSS Feeds